Using Secrets in REST Requests
As explained in Secrets, secrets are a way to store sensitive information such as API keys. You can use secrets in your REST requests to keep your API keys safe.
Both the Headers and URL Parameters sections in the REST request configuration allow you to use secrets via the s keyword.
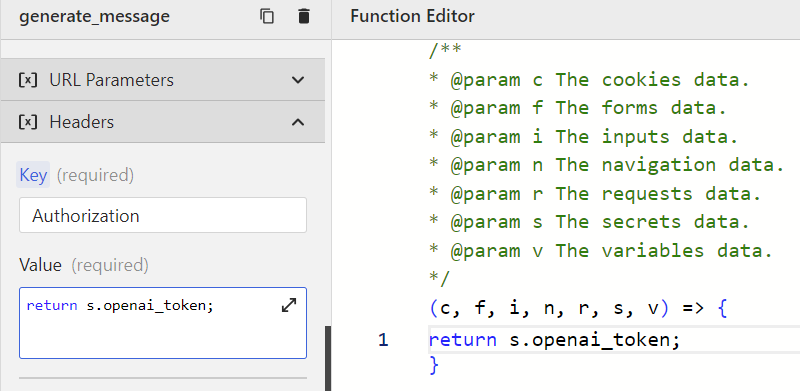
When you use the s keyword, Wized will treat the request differently and send it through its own servers, where the secret is stored.
Here is an in-depth explanatory video on how to use secrets in REST requests:
Limitations
For security reasons, Wized will only run REST Requests that have an explicit Base URL defined in the REST App. This is to prevent users from sending requests to arbitrary URLs, which could be used to perform malicious actions.
How does Wized handle secrets in REST requests?
The normal workflow when performing a REST request is as follows:
- The request is triggered by an event that happens in the browser, such as a button click.
- The request is sent to the server, directly from the user's browser.

This has a few implications:
- The request is sent from the user's browser, so the user can see the request's details, including the headers and URL parameters. This means that if you include an API key in the request, the user can see it.
- The server may not expect requests coming from a browser, which may cause CORS issues.
When you use a secret in a REST request, Wized will no longer send the request directly from the user's browser. Instead, Wized will send the request to its own servers, where the secret is stored:
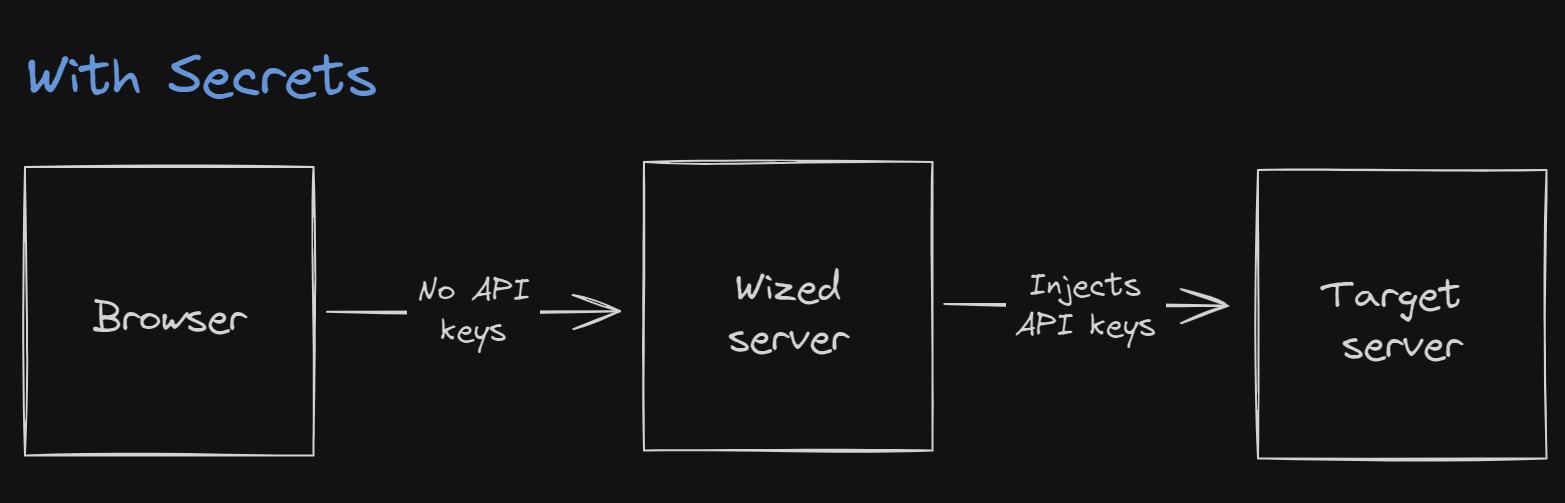
In this scenario Wized acts as a middleman, receiving the request from the user's browser, adding the secret, and then sending the request to the server. This way, the secret is never exposed to the user's browser.